Eufy cameras found to have a vulnerability, again.
Eufy has a new set of controversies it’s facing, and it deals with user’s privacy
January 23, 2023
Not many own Eufy camera’s, or even know what they are. So a quick explainer for those of you who have never heard of Eufy, they are a sub-brand of a company that is called Anker.
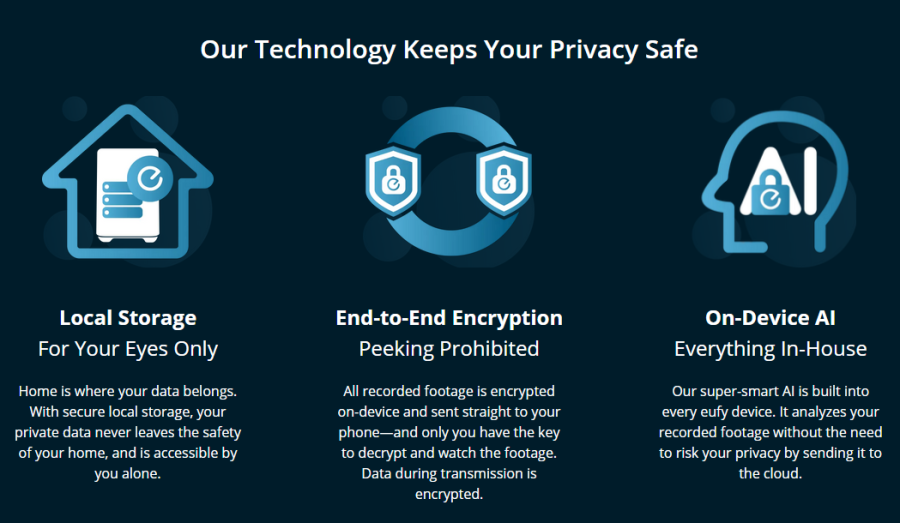
Anker makes all sorts of tech products and was highly reliable in terms of build quality on all their products. Even Eufy, the sub-company they own was highly recommended to people by reviewers. They boast that their camera streams are end-to-end military-grade encrypted meaning that no one else can access your security camera streams. On top of that streams were stored locally, with nothing being sent to the cloud. (You can view their old Privacy commitment below).
With all that being considered, these cameras sounded like a no-brainer option to choose when searching for a security camera. They had everything somebody who wanted a camera could want. That is until people found out the opposite.
On November 30th 2022, The Verge published an article entitled “Anker’s Eufy lied to us about the security of its security cameras”. In that article, technology reporter, Sean Hollister, referenced a hacker who goes by Wasabi and infosec consultant Paul Moore, who brought this to his attention.
Paul Moore and Wasabi both alleged that you could watch the Doorbell Dual camera streams unencrypted using a free open-source video player, VLC. Sean then further states that by using a unique address on Eufy’s server, that is linked to your serial number, you would be able to see your security camera stream unencrypted. When asked about this vulnerability, Brett White, a senior PR manager at Anker, told Hollister via email response, “I can confirm that it is not possible to start a stream and watch live footage using a third-party player such as VLC,” This vulnerability hasn’t yet been exploited.

This isn’t the first time that this situation has occurred. Back in 2021, Eufy had a bug that exposed over 700 customers’ security camera streams. Other Eufy users were reportedly able to access other Eufy customer streams and were able to control the cameras and view the other customer’s personal information. Eufy has since apologized for this bug and promised to do better. However, according to these allegations, Eufy has not done anything. It shouldn’t have been possible to access other people’s streams unencrypted. This controversy that Eufy is facing could’ve been avoided.
When these allegations arose, instead of answering any questions that people had, Eufy decided to change their Privacy commitment. They do have the right to do so, but ended up damaging their reputation even further. When comparing the previous Privacy commitment, to the most recent one using the Wayback Machine, the following were removed off of the website.
- We’re taking every step imaginable to ensure your data remains private, with you.”
- “Your recorded footage will be kept private. Stored locally. With military-grade encryption. And transmitted to you, and only you.”
- “With secure local storage, your private data never leaves the safety of your home, and is accessible by you alone.”
- “All recorded footage is encrypted on-device and sent straight to your phone—and only you have the key to decrypt and watch the footage. Data during transmission is encrypted.”
- “There is no online link available to any video.”
- “You need to use Eufy software and your account to decrypt the clips for viewing. No one else can access or read this data.”
Other companies are also found to have been using the same verbiage as the Privacy commitment once found on Eufy’s website. (Our family recently bought a camera that had the same wording as the privacy commitment on Eufy’s page. So, that was very interesting) According to Paul Moore, it’s generally safer to use a company that discloses that they use the cloud since their encryption tends to be better.
After weeks of silence, Eufy finally responded to these allegations with a blog post titled “To our eufy Security Customers and Partners” posted on December 19, 2022. Eufy starts by saying that their “security solutions have been designed to operate locally and wherever possible, avoid using the cloud” Which includes facial recognition, is done directly on the device. The post continues by stating that “our security technology model has never been attempted, and we expect challenges along the way. But we remain committed to the millions of consumers worldwide who have chosen Eufy Security to help protect their security, privacy, and identity”. They also state that the reason that they haven’t responded to these claims is that they were gathering all the facts before they publicly addressed these claims. Throughout this blog post, they admit that they use the cloud to send notifications. When a user chooses to include a thumbnail when getting notifications, those thumbnails are sent to the cloud, and then back to the user’s phone. Eufy claims that these images are deleted and that the process complies with industry standards. Eufy also denies sending facial recognition data to the cloud. Eufy says that the Video Doorbell Dual sends facial recognition data to the cloud to “share that initial image to other cameras on the user’s local Eufy Security system.
Eufy also acknowledges the fact that its web portal feature had a security flaw. They, however, stop short of apologizing for their mistakes. They state that this vulnerability has not been used and no user data has been exposed. They state that they changed how the web portal works. Those who want to view a live stream must log into the web portal first. Finally, they end their post stating that they are “committed to and will continue to work hard to uphold our community’s trust in our products, services, and processes.” The responses to this blog post were mostly negative, and while this was a step in the right direction, the damage has been done. Many people have lost trust in Eufy and it remains to be seen how this controversy will affect the company in the long run. The blog post also leaves many questions unanswered. The Verge brought up these important questions, and we have yet to hear back from the company.
- Why do your supposedly end-to-end encrypted cameras produce unencrypted streams at all?
- Under what circumstances is video actually encrypted?
- Do any other parts of Eufy’s service rely on unencrypted streams, such as Eufy’s desktop web portal?
- How long is an unencrypted stream accessible?
- Are there any Eufy camera models that do *not* transmit unencrypted streams?
- Will Eufy completely disable the transmission of unencrypted streams? When? How? If not, why not?
- If not, will Eufy disclose to its customers that their streams are not actually always end-to-end encrypted? When and where?
- Has Eufy changed the stream URLs to something more difficult to reverse engineer? If not, will Eufy do so? When?
- Are unencrypted streams still accessible when cameras use HomeKit Secure Video?
- Is it true that ”ZXSecurity17Cam@” is an actual encryption key? If not, why did that appear in your code labeled as an encryption key and appear in a GitHub repo from 2019?
- Beyond the thumbnails and the unencrypted streams, are there any other private data or identifying elements that Eufy’s cameras allow access to via the cloud?
- Beyond potentially tapping into an unencrypted stream, are there any other things that Eufy’s servers can remotely tell a camera to do?
- What keeps Eufy and Anker employees from tapping into these streams?
- Which other specific measures will Eufy take to address its security and reassure customers?
- Has Anker retained any independent security firms to conduct an audit of its practices following these disclosures? Which?
- Will Anker be offering refunds to those customers who bought cameras based on Eufy’s privacy commitment?
- Why did Anker tell The Verge that it was not possible to view the unencrypted stream in an app like VLC?
- Does eufy share video recordings with law enforcement agencies?
We have yet to see how this story will conclude, and how the company will further respond to these questions. An update will be made once these answers are released. For now, stay cautious about what company’s products you buy, since those privacy policies may be inaccurate as was the case with Eufy. This story is not to say that Eufy or security camera companies should be totally avoided, but a word of caution to people who use security cameras.